Key Technical Concepts
Introduction
Understanding key technical concepts is essential for effective threat intelligence analysis. This module covers fundamental technical aspects that every CTI analyst should know.
What You'll Learn
- Basic Acronyms
- Basic cryptographic concepts
- Understanding vulnerabilities
- Command & Control infrastructure
- Common intrusion vectors
Basics
A Cyber Threat Intelligence analyst must master a broad range of technical concepts. Below is a list of key areas and concepts that you will need to be familia with. I have grouped several concepts together here as they go hand in hand really.
TTPs - Tactics, Techniques & Procedures
TTPs refers to the patterns of activities or methods used by threat actors. TTPs describe how attackers operate. Tactics (high-level goals or phases of an attack). Techniques (specific methods to achieve those goals), and Procedures (concrete implementations). Mastering TTPs allows analysts to recognize adversary behaviors and attribute attacks to specific groups. Understanding TTPs is crucial for using frameworks like MITRE ATT&CK and for mapping detections to adversary behavior. We will discuss MITRE ATT&CK later in this moodule.
Picture of a Tactic, Technique and Procedure
The picture below demonstrates the relationship between TTPs.
Example of a Tactic, Technique and Procedure
IOCs - Indicators of compromise
IoCs are forensic artifacts of an intrusion – pieces of data that indicate a system may have been breached. Common IoCs include malicious file hashes (MD5/SHA-1 fingerprints of malware), suspicious IP addresses or domains (e.g., command-and-control servers) etc It is very common to see these artifacts in threat intelligence feeds. Analysts also use IoCs to pivot, for example, taking a malware file hash found on one host and searching across enterprise endpoints to see if others are compromised and the same for malicious IP/Domain indicators. Subsequently they can be blocked, monitored etc
Cyber Kill Chain
The Cyber Kill Chain is a model that outlines the typical stages of a cyberattack from an adversary’s perspective. Developed by Lockheed Martin, it breaks an attack into phases: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, and Actions on Objectives. CTI analysts use the kill chain to understand and disrupt adversaries at each stage. For more informaiton on the Kill chain and its application, check out the Cyber Kill Chain® - Developed by Lockheedmartin
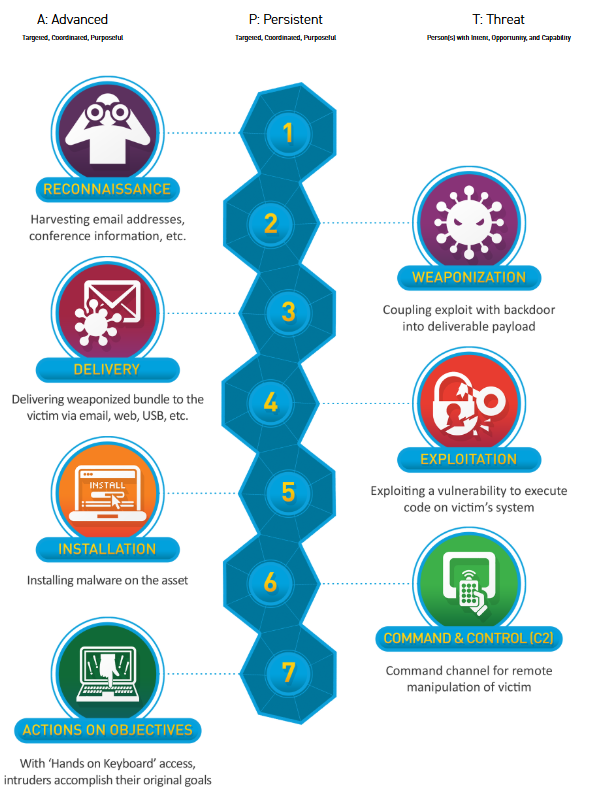
the Cyber Kill Chain®
The Unified Kill Chain
Building upon the Lockheedmartin kill chain is the unified kill chain. My personal favourite and my go to. The unified kill chain goes beyong just perimeter and incorporates a much more real-world interpretation of the stages an attacker must go through to complete their objectives. Seeing the extra amount of steps allows you to think about your own defenses in much more depth. For more information on the Unified Kill Chain visit The Unified Kill Chain

The Unified Kill Chain
Cryptography
Understanding basic cryptographic concepts and their application in cyber threats.
Symmetric Encryption
Protects data confidentiality. Uses a single key for encryption and decryption
(AES, DES, 3DES)
Asymmetric Encryption
Secure key exchange and authentication. Uses a public-private key pair
( RSA, ECC)
Hashing
Used for data integrity and verification. One-way cryptographic function
(SHA-256, MD5)
DNS
The Domain Name System (DNS) is a hierarchical, distributed database that translates human-readable domain names (e.g., www.example.com) into IP addresses (e.g., 192.168.1.1 or 2001:db8::ff00:42:8329), allowing devices to locate and communicate over the internet. Without DNS, users would have to remember numerical IP addresses instead of domain names.
Types of DNS Servers
Recursive Resolver
- Acts as an intermediary between the user and other DNS servers.
- Queries other DNS servers and caches responses.
- Examples: Google Public DNS (8.8.8.8), Cloudflare (1.1.1.1).
Root Name Server
- The highest level in the DNS hierarchy.
- Directs queries to the correct Top-Level Domain (TLD) name server.
- There are 13 logical root servers(kind of), managed by organizations like ICANN and Verisign./li>
Top-level Domain
- Stores records for domains under a specific TLD (e.g., .com, .org, .net).
- Directs queries to the appropriate authoritative name server.
Authoritative Name Server
- Stores actual DNS records for a domain.
- Provides the final answer (e.g., example.com → 192.168.1.1).
- Example: If Cloudflare manages a domain, their authoritative servers will provide the records.
Types of DNS Records
| Record Type | Purpose | Example |
|---|---|---|
| A (Address Record) | Maps a domain to an IPv4 address | example.com → 93.184.216.34 |
| AAAA (IPv6 Address Record) | Maps a domain to an IPv6 address | example.com → 2606:2800:220:1:248:1893:25c8:1946 |
| CNAME (Canonical Name Record) | Creates an alias for a domain | www.example.com → example.com |
| MX (Mail Exchange Record) | Specifies mail servers for email delivery | mail.example.com → example.com |
| TXT (Text Record) | Stores text data for verification (SPF, DKIM, etc.) | "v=spf1 include:_spf.example.com ~all" |
| NS (Name Server Record) | Specifies authoritative name servers | ns1.example.com, ns2.example.com |
| PTR (Pointer Record) | Used for reverse DNS lookups | 34.216.184.93.in-addr.arpa → example.com |
| SRV (Service Record) | Defines services available for a domain | _sip._tcp.example.com |
| SOA (Start of Authority Record) | Contains domain administration information | Primary NS, admin email, serial number |
Types of DNS Queries
Understanding the different types of DNS Queries available
Recursive Query
The DNS resolver takes full responsibility to return an answer.
If no cached response is available, it queries other servers.
Iterative Query
The DNS resolver receives partial information and follows a chain of queries.
The client queries each DNS server in steps.
Non-Recursive Queries
The DNS resolver provides cached data if available.
If no cache exists, a recursive or iterative query is performed.
Common DNS Vulnerabilities
- Attackers insert false DNS responses to redirect users to malicious sites. DNS Spoofing / Cache Poisoning
- Large-scale attacks disrupt DNS servers to take down websites such as DDoS Attacks on DNS.
- Attackers manipulate DNS settings to redirect users to fraudulent websites. DNS Hijacking for example.
- Intercept DNS queries to alter responses. (MiTM)
Fast Flux DNS
Fast Flux is a technique used by cybercriminals to hide the actual location of malicious servers by rapidly changing DNS records this makes it much more difficult to track or take down malicious websites. It is primarily used in botnets, phishing campaigns, and malware hosting to maintain resilience against takedown efforts.
The DNS A record rapidly changes, associating the domain with different IP addresses typically every few minutes. Requests to the domain are dynamically routed to different infected hosts making it difficult to block or take town the operation. The threat actors backend, which would be their command and control servers remain protected while infected machines act as intermediaries
Types of Fast Flux
- The domain’s A record (IP address) changes rapidly to different compromised machines.
- A single domain name resolves to multiple different IPs within short time intervals
- Both the A record (IP addresses) and name server (NS records) change dynamically.
- This makes it even harder to block since even the DNS infrastructure itself is volatile.
- Instead of changing IPs, new domains are rapidly generated and registered.
- Often used in malware, which generates thousands of domain names daily.
Single Fast Flux
Double Fast Flux
Domain fluxing
Uses for Fast Flux
Cybercriminals use Fast Flux to protect their malicious infrastructure from takedowns. Common uses include:
Phishing Websites
Fake banking, email, and shopping sites hosted on changing IPs.
Malware Distribution
Hosting malicious payloads using botnets.
C2 Servers
Used by botnets to maintain hidden communication with infected devices.
CSpam Networks
Used to distribute spam while preventing blacklisting of servers.
Overview of IP Protocols and Their Use in Cyber Attacks
Internet Protocol is the foundation of network communication, and different protocols operate within or alongside it to enable various functionalities. Below is a breakdown of key protocols and their security implications.
Overview of Key IP Protocols
| Protocol | Function | Usage | Security Considerations |
|---|---|---|---|
| IPv4 (Internet Protocol v4) | Provides addressing and routing for packets | Most internet traffic still runs on IPv4 | Susceptible to IP spoofing, DDoS attacks, lacks native encryption |
| IPv6 (Internet Protocol v6) | Next-gen addressing system, replacing IPv4 | Expands address space, integrates security | Potential abuse of features (IPv6 tunneling, ICMPv6 flood attacks) |
| TCP (Transmission Control Protocol) | Connection-oriented, reliable data transmission | Used for web, email, file transfer (HTTP, SMTP, FTP) | SYN flood attacks, session hijacking |
| UDP (User Datagram Protocol) | Connectionless, fast but unreliable | DNS, VoIP, streaming, gaming | UDP amplification attacks (DNS, NTP, SSDP, Memcached DDoS) |
| ICMP (Internet Control Message Protocol) | Used for network diagnostics (ping, traceroute) | Connectivity checks, error reporting | ICMP floods, smurf attacks, reconnaissance |
| PPTP (Point-to-Point Tunneling Protocol) | VPN tunneling protocol | Legacy VPN use | Weak encryption, vulnerable to MITM attacks |
| Other IP Protocols (GRE, ESP, AH, L2TP, etc.) | Various encapsulation & security protocols | VPNs, secure tunneling, specialized communication | Some may be misused for covert channels |
How Adversaries Exploit These Protocols
Adversaries often look for ways to exploit these common protocols. Below we will detail some of the common and seen exploits.
IPv4 & IPv6-Based Attacks
- IP Spoofing - Attackers forge the source IP address of packets to hide identity or bypass security.
- IPv6 Tunneling Exploits - Attackers use IPv6-over-IPv4 tunnels to evade security monitoring.
- Fragmentation Attacks - Malicious packet fragmentation to bypass firewalls and IDS/IPS systems.
TCP-Based Attacks
- SYN Flood (A type of DoS Attack) Attacker sends numerous TCP SYN requests without completing the handshake, exhausting server resources.
- PSession Hijacking - An attacker intercepts or manipulates an active TCP session
- TCP Reset (RST) Attack - Forces connection termination between two parties.
UDP-Based Attacks
- UDP Amplification Attacks - Attackers send small requests to open UDP services with spoofed source IPs, causing massive responses towards the victim.
- VoIP Exploitation - UDP-based SIP (Session Initiation Protocol) services can be attacked for toll fraud and data exfiltration
ICMP-Based Attacks
- ICMP Flood (Ping Flood / Smurf Attack) - Overwhelms a target with excessive ping requests.
- ICMP Tunneling - Attackers encapsulate data in ICMP packets to bypass firewalls.
- Reconnaissance & Network Mapping - ICMP echo requests (ping), timestamp requests, and traceroute help attackers gather intelligence on targets.
Vulnerabilities
Understanding vulnerabilities and their exploitation is crucial for defending against cyber threats. By analyzing how adversaries use vulnerabilities, security teams can detect, attribute, and mitigate attacks effectively.
Aside from the vulnreability lifecycle which is a good benchmark for how to tackle vulnerabilities within your environment there are of course some concepts specific to how threat actors use vulnerabilities.
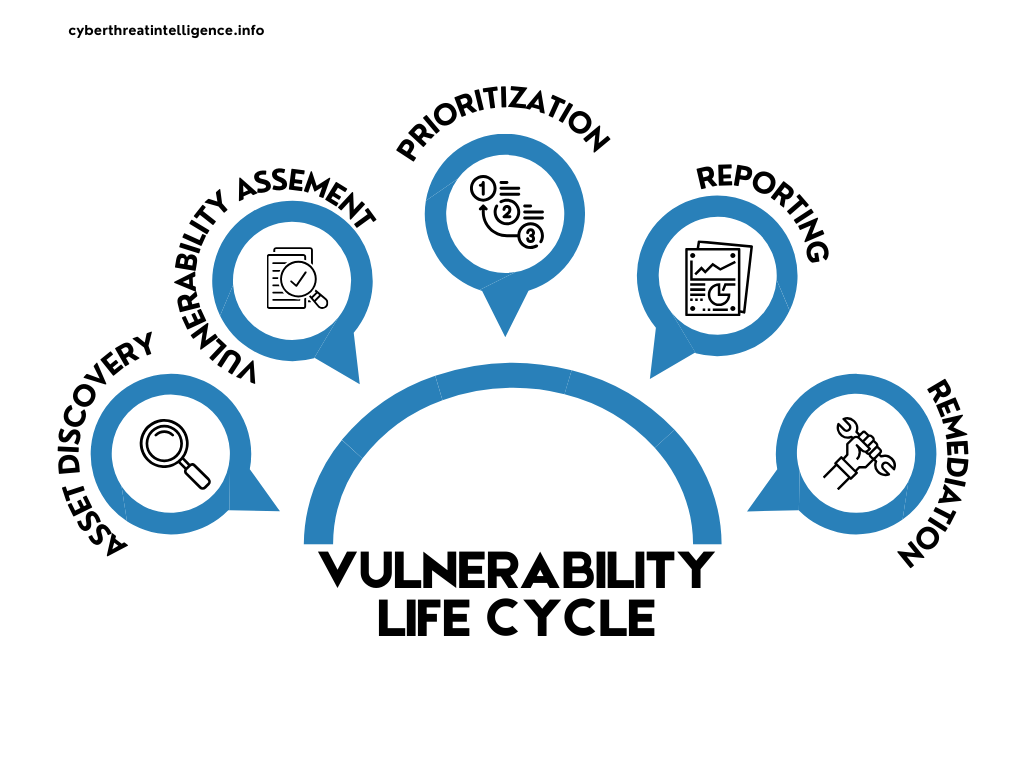
Vulnerability Lifecycle
Vulnerabilities exist across different platforms, allowing attackers to exploit them for unauthorized access, data theft, and system compromise. I will detail some of these below. I will make an assumption that most if not all you reading this are somewhat familiar different types of vulnerabilities.
Desktop Operating Systems
- Privilege Escalation
- Remote Code Execution
- Weak Default Credentials
- Unpatched Systems
Web Server and Web Application Vulnerabilities
Check the Top 10 OWASP Web Application
- SQL Injection
- Cross-Site Scripting
- Remote Code Execution
- Directory Traversal
Mobile Device Vulnerabilities
Check the Top 10 OWASP Mobile Application
- Jailbreaking/Rooting
- App-based Malware
- Insecure Data Storage
- Bluetooth/Wi-Fi Exploits
Understanding Zero-Day Exploits and Adversary Usage
A zero-day vulnerability is a flaw that has no patch available when it is first discovered. Attackers exploit these vulnerabilities before developers release a fix.
Nation-State Cyber Attacks like APT groups use zero-days for cyber espionage (e.g., Stuxnet exploiting Windows zero-days). Malware and Ransomware Delivery is used by attackers, they use zero-days to install backdoors and ransomware (e.g., CVE-2021-34527 (PrintNightmare) exploited in ransomware campaigns). Targeted Attacks on High-Value Organizations, its common that exploits are sold on the dark web or used by cybercriminals to breach critical infrastructure.
Command & Control
Command and Control or commonly abbreviated to (C2) refers to the communication infrastructure used by attackers to remotely manage compromised systems in a target environment. It enables adversaries to issue commands, execute malicious payloads, exfiltrate data, and maintain persistent access to a victim’s network.
Attackers use various methods to establish and maintain C2, we will detail some of them below.
Direct C2
- Dedicated servers
- Compromised infrastructure
- Peer to Peer
Indirect C2
- Domain fronting
- DNS tunneling
- HTTPS (Blend in)
- Cloud Based
- Social Media
- Messaging Apps
I discuss the above in detail and we use and setup some common tools to understand how these work and how attackers actually use and abuse them in my Advanced Cyber Threat Intelligence Course
Exfiltration Techniques
Common Data Exfiltration Protocols
| Protocol | Used For | Exfiltration Method | Risk Level |
|---|---|---|---|
| HTTP/HTTPS | Web traffic | Uploading stolen data to a C2 server or cloud storage | High |
| DNS | Domain name resolution | Encoding data inside DNS queries or responses | High |
| SMTP | Sending stolen files as email attachments | Medium | |
| FTP/SFTP | File transfers | Moving exfiltrated files to an external server | High |
| ICMP | Network diagnostics | Exfiltrating data using ICMP packets (Ping Tunnel) | High |
| SMB | File sharing | Moving files across network shares (internal lateral movement) | Medium |
| RDP | Remote access | Copying files via clipboard, mapped drives | High |
| Tor | Anonymity | Sending encrypted traffic over the Tor network | High |
| VPN | Encrypted tunneling | Sending stolen data over a secure tunnel | Medium |
| DNS over HTTPS (DoH) | Encrypted DNS | Hiding data inside encrypted DNS queries | High |
| Cloud Services (Google Drive, Dropbox, OneDrive) | File storage | Uploading data to attacker-controlled accounts | High |
WHOIS & IP Registration Records in CTI
| Field | Description |
|---|---|
| Registrant Information | Name, organization, email, phone number of the domain owner. |
| Registrar Details | The entity that registered the domain (e.g., GoDaddy, Namecheap). |
| Registration & Expiration Dates | When the domain was created and when it will expire. |
| Name Servers | DNS servers responsible for resolving the domain. |
| Domain Status | Indicates whether the domain is active, expired, locked, or transferred. |
| Associated IP Addresses | Links the domain to hosting infrastructure. |
| IP Range Ownership | The organization or ISP assigned to an IP range. |
| Contact Details for Abuse Reporting | Email or phone numbers for reporting abuse related to an IP or domain. |
| Autonomous System Number (ASN) | Identifies the network block and provider managing the IP. |
CTI Use Cases for WHOIS & IP Records
Threat Actor Attribution
- Identifying common registrants or shared infrastructure across malicious domains.
- Pivoting on contact details or email addresses used in past campaigns.
Malicious Domain & Infrastructure Tracking
- Investigating newly registered domains used in phishing, malware, or C2 servers.
- Monitoring for typo-squatting or brand impersonation domains.
Takedown & Legal Actions
- Reporting abuse to registrars or ISPs to disable malicious domains or IPs.
- Assisting law enforcement with evidence collection.
Supply Chain & Vendor Risk
- Checking if vendors use secure domain registrations (e.g., avoiding free email providers).
- Identifying domains that might be typosquatted versions of legitimate vendors.
Dark Web & Fraud Investigation
- Investigating domains linked to cybercriminal forums, data dumps, or scam operations.
- Correlating WHOIS records with leaked databases to identify threat actors.
Attack Surface Management
- Discovering shadow IT assets through domain and subdomain enumeration.
- Identifying infrastructure linked to an organization's domains.