Threat Analysis Methodologies & Bias
Introduction
Cyber Threat Intelligence analysis methodologies provide structured approaches to processing raw threat data, transforming it into actionable insights that security teams can use to detect, prevent, and respond to attacks. These methodologies help analysts classify threats, attribute attacks to known adversaries, predict future threats, and assess potential risks to organizations.
By leveraging frameworks such as the ones we will discuss later intelligence teams can systematically map adversary behavior, track attack patterns, and enhance threat-hunting efforts. Understanding and applying these methodologies enables organizations to stay ahead of emerging threats, strengthen their defenses, and make intelligence-driven security decisions.
Understanding different threat analysis methodologies is crucial for effective cyber threat intelligence. This module covers the most important frameworks used in the industry.
What You'll Learn
- Understanding bias
- Diamond Model
- ACH
- IPB/IPE
- Forecasting / Horizon Scanning
- When to use each methodology
Bias
Bias is an inherent challenge in Cyber Threat Intelligence analysis that can distort findings, mislead decision-making, and result in incorrect threat attribution. Cognitive biases, influenced by personal experience, organizational culture, or external factors can affect how analysts interpret threat data, leading to confirmation bias, overconfidence, or faulty assumptions.
Analytical biases arise from structured methodologies, intelligence gaps, or the way data is presented, potentially shaping perceptions of adversaries, risks, or attack attribution. Recognizing and mitigating bias is essential to ensuring that intelligence assessments remain objective, data-driven, and actionable.
Common Biases in Cyber Threat Intelligence Analysis
| Bias Type | Description | Impact on Threat Intelligence | Mitigation Strategies |
|---|---|---|---|
| Confirmation Bias | Seeking or interpreting information that confirms preexisting beliefs. | Analysts may dismiss contradictory evidence when attributing an attack. | Use ACH (Analysis of Competing Hypotheses) to weigh all possibilities objectively. |
| Anchoring Bias | Relying too heavily on initial information when making decisions. | Sticking to an early attack attribution without considering new evidence. | Regularly reassess assumptions as new intelligence emerges. |
| Overconfidence Bias | Overestimating the accuracy of one’s analysis or predictions. | Assuming an attack is state-sponsored without sufficient proof. | Encourage peer review and red teaming to challenge assessments. |
| Recency Bias | Giving more importance to recent events over historical data. | Over-prioritizing new ransomware strains while ignoring older, persistent threats. | Use historical trend analysis to compare with past attack patterns. |
| Availability Bias | Relying on easily accessible intelligence rather than complete data. | Focusing on widely reported threats while missing underreported but critical risks. | Incorporate diverse intelligence sources (OSINT, HUMINT, SIGINT). |
| Attribution Bias | Assigning intent or blame based on geopolitical or organizational assumptions. | Misattributing cyber attacks to adversaries without solid forensic evidence. | Use technical indicators (MITRE ATT&CK, TTP correlation) instead of assumptions. |
| Groupthink | Conforming to a consensus within an intelligence team, even if flawed. | Accepting a dominant analysis perspective without question. | Encourage devil’s advocacy, alternative analysis techniques. |
| Hindsight Bias | Believing an attack was predictable after it has occurred. | "We should have seen this coming" mentality, leading to unrealistic expectations. | Focus on proactive threat intelligence, not retrospective blame. |
| Survivorship Bias | Focusing only on successful attacks while ignoring missed attempts. | Assuming all threats are sophisticated, ignoring blocked or failed attacks. | Analyze all attack attempts, including unsuccessful intrusions. |
There is a lot more to be said about biases (and there is more that I could list) I would recommend using google and reading about all the different types to get a good understanding of how they could impact your analysis.
So, how can we reduce bias in our analysis?
- Use structured analytical techniques (ACH, Bayesian analysis, Red Teaming)
- Encourage diverse perspectives and peer reviews in intelligence assessments
- Avoid premature attribution—rely on technical evidence, not assumptions
- Train analysts in cognitive bias awareness
Diamond Model
The Diamond Model of Intrusion Analysis is a cyber threat intelligence framework designed to analyze and understand cyber intrusions systematically. Developed in 2013 by Sergio Caltagirone, Andrew Pendergast, and Christopher Betz, the model provides a structured way to connect adversary actions, tools, infrastructure, and victims. This approach helps track threats, attribute attacks, and predict future behavior by analyzing how different elements of an intrusion relate to one another.
I highly recommend you read the white paper HERE I certainly won't be covering it indepth. The Diamond Model is built from Axioms. I am not going to go through them all here, I will briefly describe the basic model.
1️⃣ Axiom 1: Every Intrusion Has an Adversary and a Victim
2️⃣ Axiom 2: There Exists a Relationship Between the Adversary and the Capability Used
3️⃣ Axiom 3: There Exists a Relationship Between the Adversary and the Infrastructure Used
4️⃣ Axiom 4: There Exists a Relationship Between the Capability and the Infrastructure Used
5️⃣ Axiom 5: An Adversary’s Intent is Pursued Through a Phase-Based Methodology/p>
6️⃣ Axiom 6: The Diamond Model is Recursive & Expansive
Adversary
The threat actor conducting the operation
Capability
Tools and techniques used by the adversary
Infrastructure
Physical and logical communication structures
Victim
Target of the adversary's operations
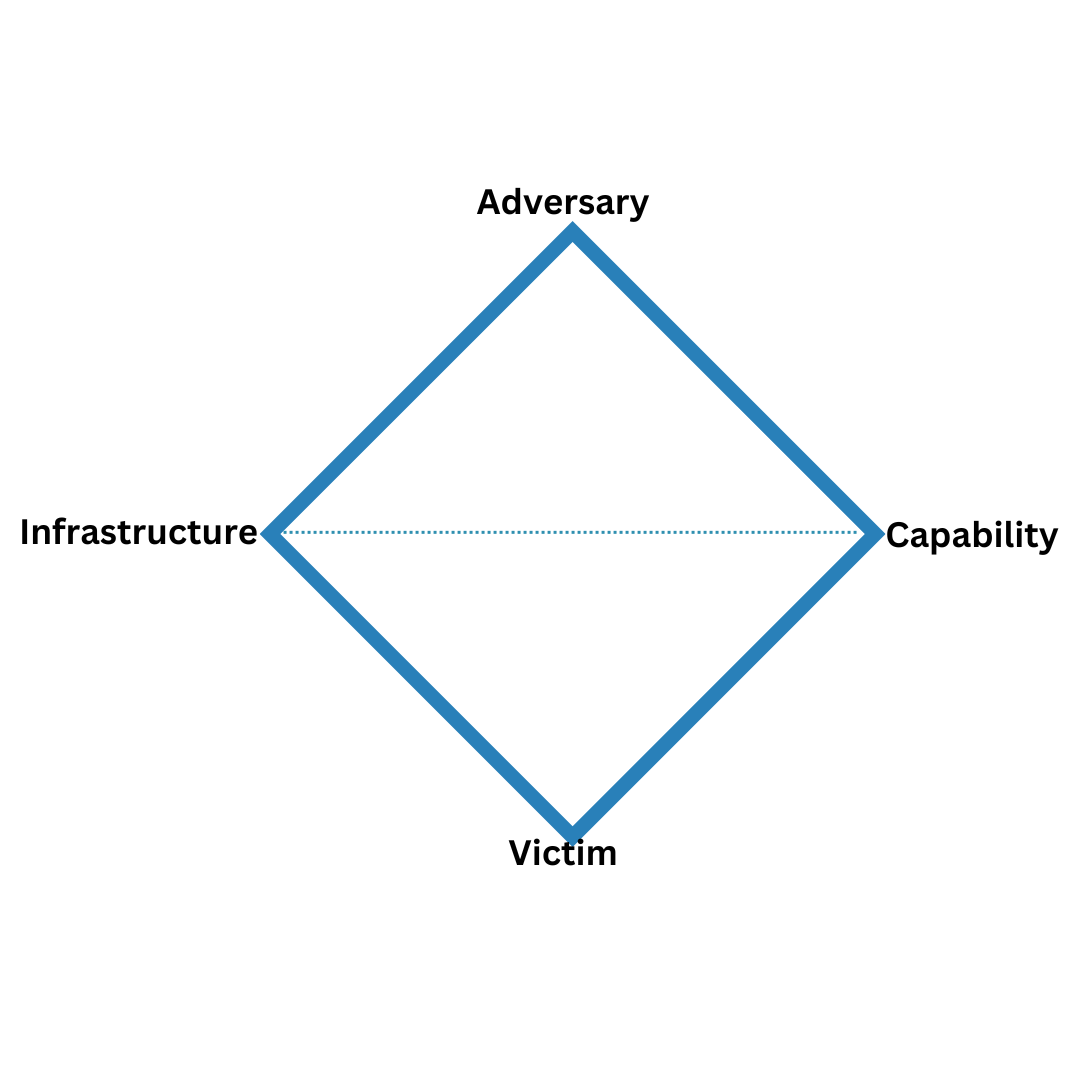
Figure 1: The Diamond Model of Intrusion Analysis
How the Diamond Model is Used in Threat Intelligence
- Threat Attribution – Identifying which adversary is responsible for an attack.
- Intrusion Analysis – Understanding the tools, techniques, and infrastructure used.
- Threat Hunting – Tracking patterns across multiple attack incidents.
- Attack Disruption – Identifying and mitigating key attack components.
A key advantage of the Diamond Model is its pivoting ability, allowing analysts to connect different threat components:
- 1️⃣ Pivot from Victim to Infrastructure → Identify malicious IPs, domains, and C2 networks.
- 2️⃣ Pivot from Infrastructure to Capability → Determine what malware or exploits are being used.
- 3️⃣ Pivot from Capability to Adversary → Match tactics with known threat actor groups (e.g., MITRE ATT&CK).
Strengths and Weaknesses of the Diamond Model
| Strengths | Weaknesses |
|---|---|
| Provides a structured way to analyze cyber intrusions, linking adversaries, infrastructure, capabilities, and victims. | Requires high-quality intelligence to fully map all four elements. |
| Facilitates pivoting across different threat elements, helping analysts track attack evolution. | Does not inherently analyze attack progression over time (needs to be paired with Cyber Kill Chain or MITRE ATT&CK). |
| Enhances threat attribution by correlating TTPs, adversaries, and infrastructure. | Lacks built-in automation—requires manual intelligence gathering and analysis. |
| Can be applied recursively, allowing expansion of analysis over multiple intrusion campaigns. | Focused more on tactical and operational intelligence rather than strategic intelligence. |
| Works well in conjunction with MITRE ATT&CK and other frameworks to strengthen threat hunting. | Not designed to handle insider threats or non-traditional cyber attacks effectively. |
Analysis of Competing Hypotheses
The Analysis of Competing Hypotheses (ACH) is a structured analytical method designed to reduce cognitive bias and ensure objectivity when evaluating multiple possible explanations for an event or incident. Developed by Richard Heuer, ACH forces analysts to consider all possible hypotheses, rather than defaulting to the most convenient or familiar explanation. Again, I would highly recommend you study the witepaper to get the very best from ACH. HERE
Purpose in Cyber Threat Intelligence
- Helps determine the most likely cause of an intrusion.
- Assists in threat attribution
- Threat Hunting – Tracking patterns across multiple attack incidents.
- Reduces confirmation bias and anchoring bias in intelligence assessments.
Lets just jump straight into an example, I think this is the easiest way to grasp the concept.
8-Step ACH (Analysis of Competing Hypotheses) Process
| Step | Description | Why It Matters |
|---|---|---|
| 1. Identify the Problem | Clearly define the question or issue being analyzed. | Prevents analysts from chasing the wrong questions or making unfounded assumptions. |
| 2. Generate Alternative Hypotheses | List all possible explanations, even unlikely ones. | Forces analysts to consider multiple perspectives rather than defaulting to the most obvious one. |
| 3. List Evidence & Assumptions | Gather all relevant data and list key assumptions. | Ensures that the analysis is based on facts, not intuition or bias. |
| 4. Analyze Evidence Against Each Hypothesis | Compare which pieces of evidence support or contradict each hypothesis. | Highlights weak hypotheses that should be eliminated early. |
| 5. Remove Inconsistent Hypotheses | Eliminate explanations that contradict the available evidence. | Prevents confirmation bias where analysts favor their initial assumptions. |
| 6. Evaluate Confidence Levels | Assess how reliable the remaining hypotheses are based on the strength of the supporting evidence. | Forces realistic assessments rather than overconfidence in a weak conclusion. |
| 7. Report Findings | Document the conclusion with clear evidence and any remaining uncertainties. | Ensures accountability and helps decision-makers understand the level of confidence in the analysis. |
| 8. Monitor & Reassess | Continue collecting intelligence and update the analysis as new data emerges. | Prevents intelligence teams from locking into outdated conclusions. |
Now lets take a very simple example to explain how this would work. Lets pick a fairly simple scenario.
Scenario
Made up corp experienced a targeted cyberattack involving data exfiltration and the deployment of custom malware. Analysts must determine the most likely threat actor responsible.
Ask the Question, or What is the Question?
Who is responsible for the cyberattack on made up corp? Lets quickly build some hypotheses and list them out in a table for easy reference and viewing.
| Hypothesis (H) | Possible Threat Actor | Description |
|---|---|---|
| H1 | APT29 (Russian State-Sponsored) | Russian intelligence group known for cyber-espionage, highly sophisticated attacks, and targeting government and corporate entities. |
| H2 | APT41 (Chinese State-Sponsored) | China-based group engaged in both espionage and financially motivated attacks, known for supply chain compromises. |
| H3 | FIN7 (Cybercriminal Group) | Organized cybercrime group specializing in financial fraud, ransomware, and point-of-sale (POS) malware. |
| H4 | Insider Threat | A malicious or compromised employee leaking data or aiding external attackers. |
| H5 | Hacktivists | Politically or ideologically motivated hackers aiming for disruption or public exposure. |
Now we can start to assess each hypotheses against a number of existing factors, TECHINT etc
Step 3: Identify & Evaluate Evidence
| Evidence (E) | H1: APT29 (Russia) | H2: APT41 (China) | H3: FIN7 (Cybercrime) | H4: Insider Threat | H5: Hacktivists |
|---|---|---|---|---|---|
| E1: Custom malware linked to past intrusions | ✅ Matches known APT29 tools | ✅ Some overlap with APT41 malware | ❌ FIN7 prefers off-the-shelf malware | ❌ Insiders rarely develop custom malware | ❌ Hacktivists lack resources for custom tools |
| E2: Target is a government contractor | ✅ APT29 often targets government sectors | ✅ APT41 also targets high-value institutions | ❌ FIN7 focuses on financial data | ❌ Insider threat unlikely given the scale | ❌ Hacktivists rarely target private companies |
| E3: C2 servers linked to prior espionage campaigns | ✅ C2 infrastructure previously linked to APT29 | ✅ Some domains match APT41 patterns | ❌ FIN7 uses bulletproof hosting, no known links | ❌ Insiders do not typically use C2 infrastructure | ❌ Hacktivists favor public communication channels |
| E4: TTPs (MITRE ATT&CK mapping) | ✅ Matches APT29’s known TTPs | ✅ APT41 also shares some techniques | ✅ Some overlap, but financial motive is missing | ❌ Insider methods do not align | ❌ Hacktivist techniques differ significantly |
| E5: Ransom demand or financial motive? | ❌ No ransom request, espionage focus | ❌ No financial motive | ✅ FIN7 operates for financial gain | ❌ Insider motive unclear | ❌ Hacktivists are not financially motivated |
| E6: Geopolitical context | ✅ Increased Russian cyber activity against Western targets | ✅ China known for intellectual property theft | ❌ FIN7 lacks geopolitical objectives | ❌ No geopolitical indicators of insider involvement | ✅ Hacktivists may be involved if a political factor exists |
| E7: Attack timeline (Dwell time in network) | ✅ APT29 known for persistent, stealthy attacks | ✅ APT41 also uses persistent techniques | ❌ FIN7 usually operates quickly | ✅ Possible long-term insider access | ❌ Hacktivists prefer quick, disruptive attacks |
Now we have a fairly good list with evidence we can start to elimiate hypotheses that conflict with evidence. So as an example we could say (Fin7) is dismissed as there is no financial motive and no ransom demand. Insider could be dismissed as there is no evidence of exfiltration from within and whilst we're at it, we can remove Hacktivits as the attack lacks the characteristics which are associated with hacktivist campaigns.
Next we would move on to refinement and determin the most likely hypotheses and probably associate a confidence level to that process. With our particular example, APT29 seems to have the strongest evidence alignment, closely followed by APT41 with some TTP overlap. So our final assessment and conclusion would be APT29 is the most likely adversary
Why Use ACH in Threat Intelligence?
- Removes bias – Ensures that all possibilities are explored rather than jumping to conclusions.
- Improves accuracy – Helps eliminate weak hypotheses and focus on the most probable adversary.
- Works well with other CTI models – Can be combined with MITRE ATT&CK, Diamond Model, and Cyber Kill Chain for a complete threat picture.
- Supports decision-making – Helps decision makers respond to threats with higher confidence.
Intelligence Preparation of the Battlefield/Environment (IPB/IPE) in Cyber Threat Intelligence
Intelligence Preparation of the Battlefield (IPB) and its cybersecurity adaptation, Intelligence Preparation of the Environment (IPE), are structured methodologies used in intelligence and military operations to assess, predict, and counter adversarial activities.
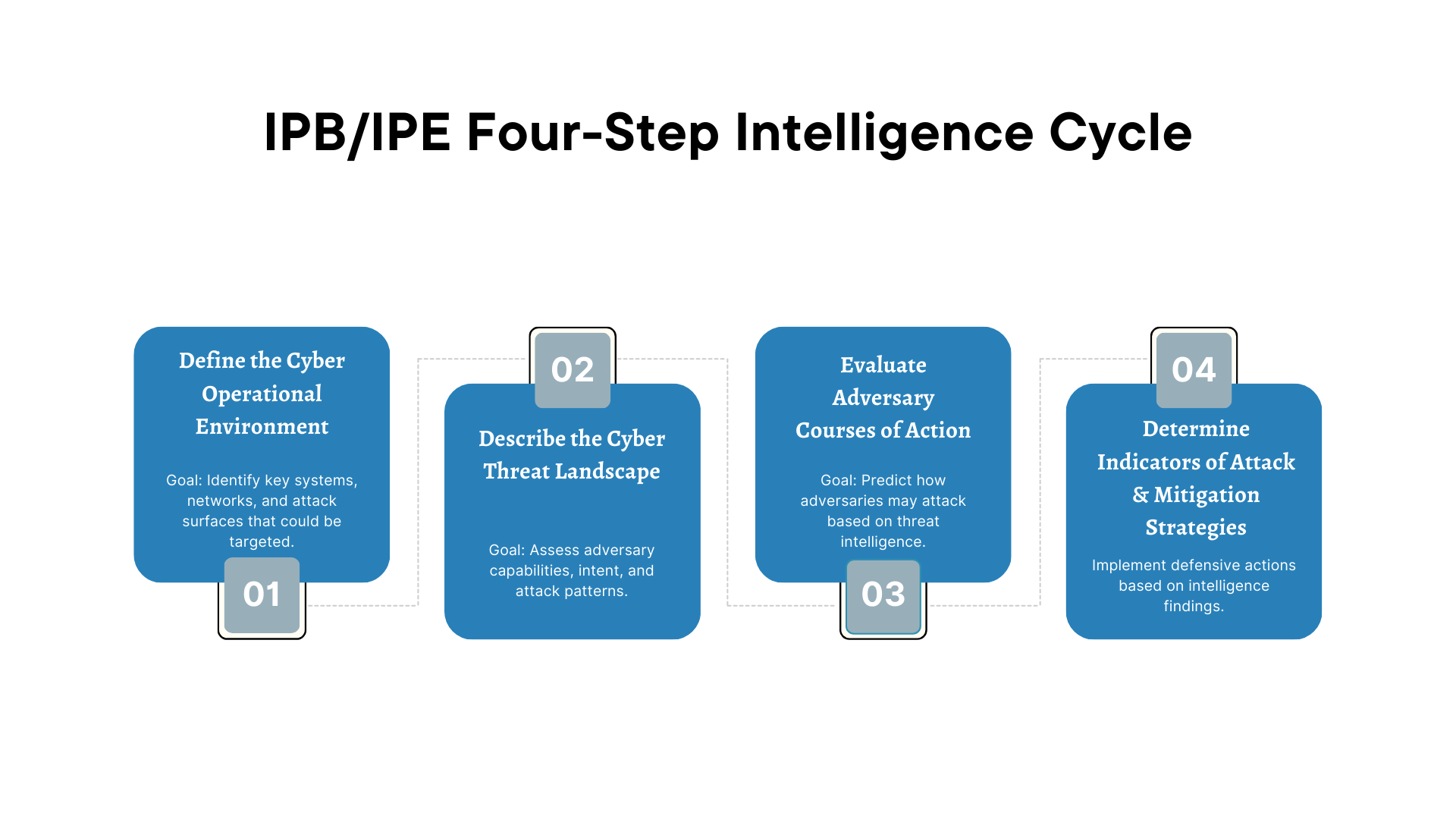
The Intelligence Preperation of the Battlefield Stages
Key Differences
- IPB (Battlefield Focus) – Traditionally used in military operations to analyze physical battlespaces.
- IPE (Environment Focus) – Adapted for cyber operations to assess threat landscapes, attack surfaces, and adversary behavior
Purpose in Cyber Threat Intelligence
- Identifies cyber threats and their potential targets.
- Maps threat actor capabilities, attack surfaces, and defensive gaps.
- Supports proactive cyber defense by anticipating threat vectors before an attack occurs.
- Enhances threat attribution and response planning.
Step 1: Define the Cyber Operational Environment
Goal: Identify key systems, networks, and attack surfaces that could be targeted.
Identify critical cyber terrain
Cloud infrastructure, VPNs, DNS, email servers
Map assets and dependencies
Third-party services, supply chain vendors
Determine threat exposure
Internet-facing systems, software vulnerabilities
Identify legal & compliance concerns
GDPR, NIST, ISO 27001 regulatory impact
Step 2: Describe the Cyber Threat Landscape
Goal: Assess adversary capabilities, intent, and attack patterns.
Identify potential threat actors
APT29 (Russia), FIN7 (cybercriminals), insider threats
Analyze known TTPs
MITRE ATT&CK mapping of APT behaviors
Map existing vulnerabilities to known exploits
Log4Shell, ProxyShell, PrintNightmare
Assess PESTEL-M/STEMPLE
Specific to Social, Technological, Economic, Military, Political, Legal, Environmental
Step 3: Evaluate Adversary Courses of Action
Goal: Predict how adversaries may attack based on threat intelligence.
Define likely attack vectors(MLCoA's & MDCoA's)
Phishing, RDP brute force, supply chain compromise
Identify preferred malware & exploits
TrickBot, Cobalt Strike, APT custom implants
Assess adversary motives
Financial gain (ransomware), espionage (nation-states)
Predict attack timelines & dwell time
Fast smash-and-grab vs. long-term persistent threats
Step 4: Determine Indicators of Attack & Mitigation Strategies
Goal: Implement defensive actions based on intelligence findings.
Define Indicators of Compromise (IoCs)
Malicious IPs, file hashes, DNS activity
Deploy network & endpoint monitoring rules
SIEM alerts for anomalous traffic - etc
Strengthen identity & access controls
Enforcing MFA, least privilege access
Conduct Red Team exercises
Simulating APT attacks to test resilience
Forecasting Methodologies
Forecasting in cyber threat intelligence is the process of predicting future cyber threats, adversary behaviors, and attack trends based on historical data, emerging trends, and analytical models. It helps organizations stay ahead of threats by enabling proactive defense strategies rather than reactive responses.
There are many forecasting methodologies, I will only go through a couple of my favourites in this free course. In my paid course CTI MASTER we will put some of these forecasting methods into real world practice. We will also see the cones of plausibility in action from my platform ThreatInsights
As I will only be discussing a few and probably not doing them justice, I highly receommend you purchse the following book Structured Analytic Techniques for Intelligence Analysis
Cones of Plausibility
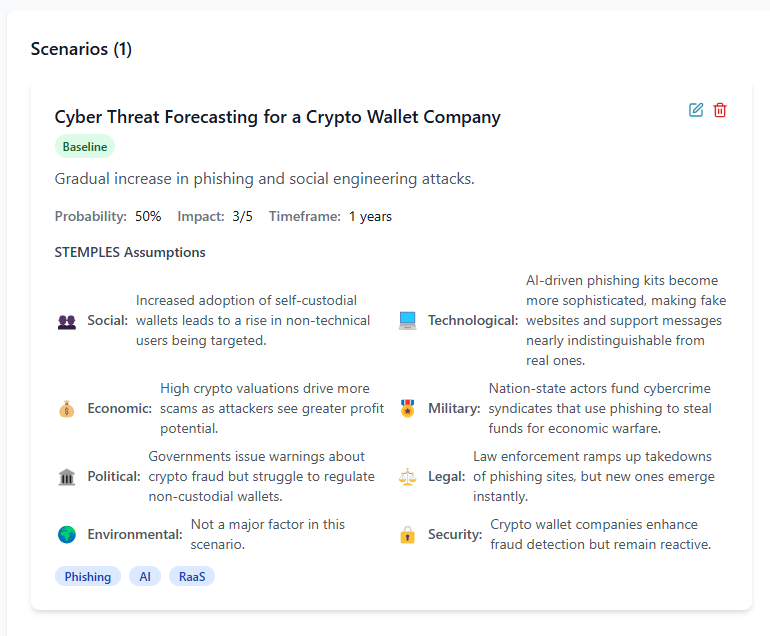
The Intelligence Preperation of the Battlefield Stages
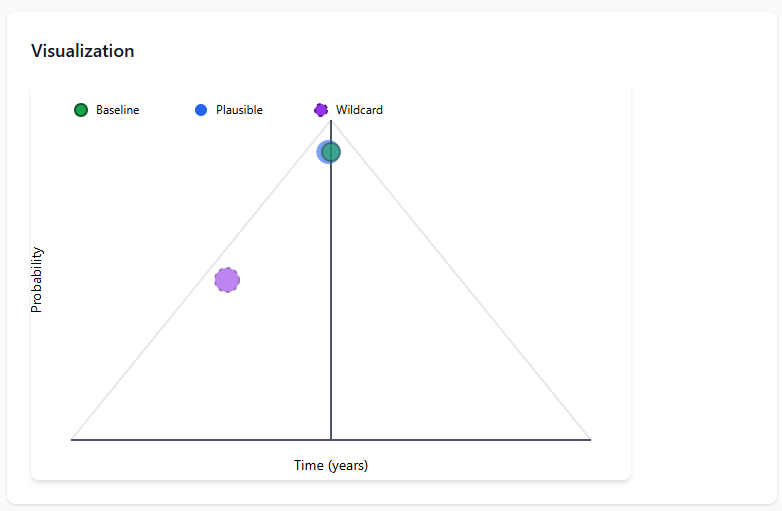
The Intelligence Preperation of the Battlefield Stages
Baseline Scenario
This is the most probable outcome based on current trends, intelligence, and observable threat activity.
Plausible Scenario
These consider plausible deviations from the baseline, often influenced by unexpected factors like geopolitical events, technological advancements, or shifts in adversary tactics.
Wildcard Scenario
These represent extreme, unexpected events that could drastically change the threat landscape, such as a major cyber-physical attack, a disruptive AI-driven attack vector, or the collapse of a major cybersecurity vendor.
How It’s Used in Cyber Threat Intelligence
Strategic Forecasting
Helps organizations prepare for emerging threats by identifying potential shifts in attacker behavior. Aids in long-term cybersecurity planning and investment decisions.
Attack Path Prediction
Security teams can map out possible future adversary attack paths based on current TTPs and trends in MITRE ATT&CK.
Proactive Defense Strategy
By considering multiple future threat scenarios, organizations can implement defenses against not only known threats but also potential emerging ones.
Ssenario based threat modeling
Used in war-gaming and red teaming exercises to test an organization's resilience against different types of cyber threats.