Threat Intelligence Lifecycle
Introduction
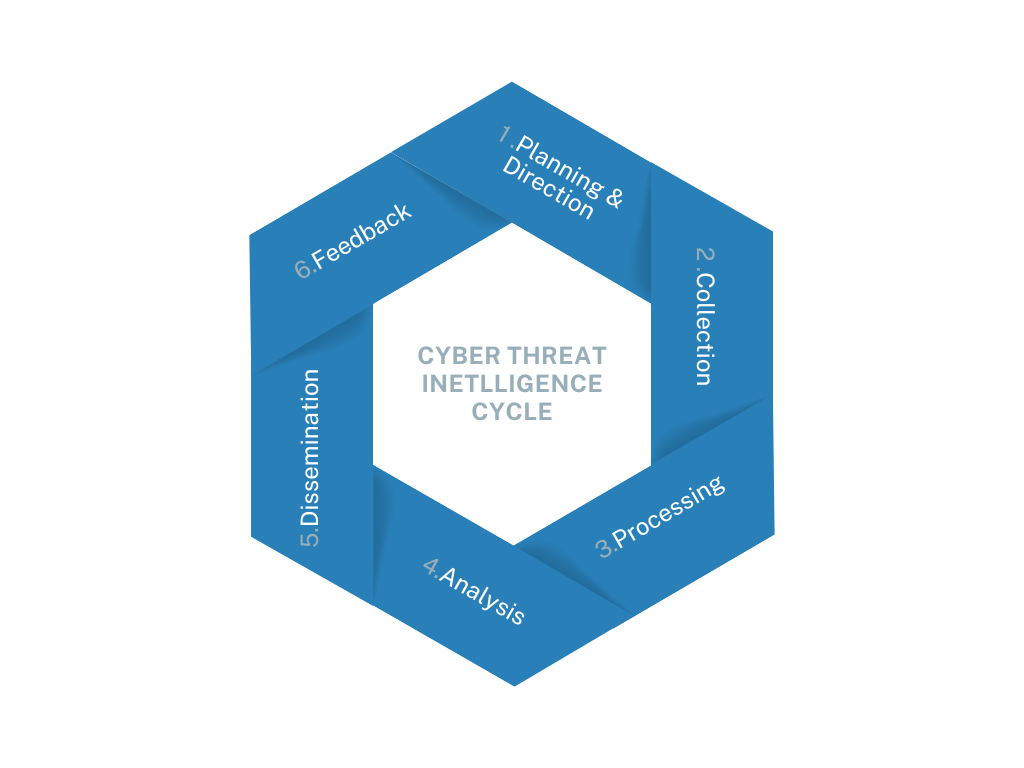
The Threat Intelligence Lifecycle is a systematic process that ensures the effective creation and management of intelligence. This module explores each phase in detail and how they work together to create actionable intelligence. You may see the model with less or more stages in it. They are all correct, I have used the one which displays the most phases to exapnd further. To avoidd confusion you will also see the Intelligence Lifecycle model with the following. (Direction, Collection, Analysis, Dissemination, Feedback)
Planning and Direction Phase Overview
What You'll Learn
- The six phases of the intelligence lifecycle
- How to implement each phase effectively
- Common challenges and solutions
- Best practices for each phase

Planning and Direction
This is the first phase of the lifecycle which focuses on defining intelligence requirements and planning the collection strategy, also this is really where we want to be setting out the high level objectives
Some things I think are important to consider at this stage and "get out of the way" first are what constraints could there be? For example, What role will the intelligence function take? Will it be to inform decisions or make decisions. Will it be able to meet its customers proposed needs due to legal, ethical or practical constraints? Who will/has the accountability and ownership of the intelligence funciton? Of course, all these questions can be easily answered by discussing them with the right stakeholders.
Customer requirements are generally broken down. Long terms directives, Medium term directives and short term directives, which we shal disuss later in this section.
- ✔ Goal: Define what intelligence is required, why it's needed, and how it will be used.
- ✔ Outcome: A structured intelligence plan that aligns with business objectives and security priorities.
The Direction phase is where intelligence operations begin. It involves identifying and prioritizing intelligence requirements to ensure that intelligence collection and analysis efforts are aligned with the organizational needs. There should be nothing random happening, it should all be planned effectively. All intelligence picked for collection should have an end purpose.
You will want to begin making sure you are able to get all the appropriate key stakeholders together. Direction initially will come from them ( The Customer) The customer(s) will be the ones consuming the intelligence. At this stage you will also define how the intelligence will be presented and disseminated.
It is important to note that sometimes the customer does not know what they need, or might think they need A but require B, or they may have a great understanding. It is our job as intelligence producers to understand the reasons for the requirement in the first place. We need to be able to elicit requirements and understand the customers mind set to better align with their goals.
To help us navigate this with a client we can use the MoSCoW method or something similar which will allow appropriate planning to take place with something that is well understood by most organisations. If you're not familiar with MoSCoW then check out this link This method helps intelligence teams rank PIRs based on their urgency, impact, and relevance. We can then use the SMART method to ensure that PIRs are well-defined, actionable, and measurable by making them
Understanding how customers consume and apply threat intelligence is essential for delivering actionable intelligence that aligns with their security operations, risk management strategies, and compliance requirements. Before mapping intelligence consumption, CTI teams must assess customer requirements, which vary based on industry, security maturity, and threat landscape.
Customer Requirements
- ✔ Industry-Specific Risks, Financial institutions vs. healthcare organizations have different threat priorities.
- ✔ Regulatory & Compliance Needs, CBEST, TIBER-EU, GDPR, NIST, ISO 27001 compliance may drive intelligence consumption.
- ✔ Organizational Maturity, Is the customer mature with a SOC, TIP, and automated feeds, or do they rely on manual processes?
- ✔ Decision-Making Levels, Intelligence must be tailored to different stakeholders (SOC teams, CISOs, risk managers, executive boards).
Examples can be varying. But a few could be, a SOC analyst needs real-time tactical threat feeds to block active threats. a CISO needs strategic intelligence reports for board level risk assessments, or a Risk Manager required long-term trend analysis to inform security investments.
Different teams within an organization consume and apply threat intelligence differently. Intelligence must be structured to ensure it reaches the right people in the right format. We will discuss this a length in this section.
Understanding the Customer’s Security Position & Requirements
Before defining scope, CTI teams must assess the organization’s current threat landscape, security maturity, and intelligence needs. I like to do this by asking very basic questions, som examples below
- ✔ What are the biggest security concerns for leadership (CISO, risk teams, SOC) What is the business priorities?
- ✔ What controls, logging, and detection capabilities are already in place?Existing defenses are useful to understand? Are the existing defenses capable, well configured?
- ✔ Does the organization have a SOC, TIP, SIEM, or intelligence-sharing capability?What is the current security maturity level? Is a prgramme of work underway?
- ✔ Compliance with CBEST, TIBER-EU, GDPR, ISO 27001, NIST CSF. Is there any lean on Industry or Regulatroy needs? Is the business in a highly regu;ated industry.
Scoping the Intelligence Project to Achieve Key Outcomes
We will be delving into this topic in much more depth depth within this chapter. But for a quick overview we will cover some points below to get you thinking.
- ✔ What will be the primary cyber threat intelligence objective?
- ✔ Who will be the consumers of the intelligence?
- ✔ What intelligence sources will be used?
- ✔ Will there be any operational security requirements?
- ✔ How will you deliver the output?
Accurate Timescale Scoping & Resource Planning
Effective threat intelligence projects require careful planning of time, personnel, and technical resources.
- ✔ What will be the urgency of the intelligence? Long/short term?
- ✔ How frequently will it be delivered? Daily, Weekly etc
- ✔ How big will the team be? What skillsets are required?
- ✔ What data processing power will be needed? Will it be bulk data or specific?
Defining Rules of Engagement, Limitations & Constraints
Rules of engagement (RoE) ensure CTI activities follow legal, ethical, and operational guidelines. Here are some considerations
- ✔ What legal frameworks must be followed?
- ✔ What intelligence methods will be approved? Passive/Active etc
- ✔ Are there any geographical restrictions?
- ✔ How long can you collect and store intelligence?
- ✔ What are the reporting and escalations procedures?
Requirements Overview
Key Explicit Requirements
Explicit requirements are clearly defined, directly stated, and formally documented intelligence needs. They are often provided by stakeholders, regulatory bodies, or business leadership and are typically tied to specific risks, compliance mandates, or operational security goals. The characteristics are clearly defined and measurable.
- ✔ Stated in formal intelligence requests, compliance documents, or business policies.
- ✔ Have direct implications for intelligence collection and reporting.
Examples
- “Monitor dark web forums for stolen corporate credentials and report findings weekly.”
- “Identify ransomware groups targeting the financial sector in Q2.”
Implicit Requirements
Implicit requirements are unstated, inferred, or indirectly necessary for fulfilling intelligence objectives. They may arise during intelligence collection, analysis, or from contextual understanding of an organization’s threat landscape. Not directly stated but inferred from explicit requirements
- ✔ Arise based on evolving threats, trends, or intelligence gaps.
- ✔ Often derived from past experiences, industry best practices, or analyst intuition.
Examples
If an explicit requirement states, “Monitor for ransomware threats against our cloud infrastructure,” an implicit requirement could be:
- “Assess vulnerabilities in third-party cloud service providers that attackers might exploit.”
- “Track emerging ransomware TTPs that target cloud storage systems.”
Essential Elements of Information
(EEI) Essential Elements of Information help break down broad intelligence questions into specific and measurable data points.
Understanding how to define and apply EEIs effectively is a key skill for Cyber Threat Intelligence.
Essential Elements of Information (EEIs) are critical intelligence data points required to satisfy Priority Intelligence Requirements (PIRs) and guide threat intelligence collection efforts. They help intelligence teams focus on specific data sets that provide actionable insights.
In the context of Cyber Threat Intelligence (CTI), EEIs act as the building blocks that support both Explicit and Implicit Intelligence Requirements, ensuring intelligence teams collect only relevant, high-value information rather than overwhelming security teams with excessive, unstructured data.
EEI's Example Structure
- 🔹 Explicit Requirement: "Identify ransomware groups targeting financial institutions."
- 🔹 Implicit Requirement: "Analyze attack vectors used by these ransomware groups."
Corresponding EEI's
- ✔ Which ransomware groups are active? (Threat Actor Profiling)
- ✔ What TTPs (Tactics, Techniques, and Procedures) do they use? (Mitre ATT&CK Mapping)
- ✔ What malware variants are associated with these groups? (YARA Rules, Malware Hashes)
- ✔ Which industries/geographies are most affected? (Target Sector Analysis)
- ✔ Which IPs, domains, and C2 infrastructure are linked? (Technical Indicators of Compromise - IoCs)
Introduction to Priority Intelligence Requirements (PIRs)
Now we have broken down how requirements can be formed, we now need to create PIR's. Priority Intelligence Requirements. Fundementally we should now have a set of well thought out and understood requirements. The task now is to place these requirements in a an order of priority. Generally, as already mentioned, these can be broken down into Long-term, Medium-term and Short-terms requirements. The key here really is to understand that it's likely not all intelligence requirements can be met, nor sufficient data can be collected, so whilst choosing the priority we also have to fator in the practicality.
PIRs help intelligence teams prioritize data collection, focus analytical efforts, and align intelligence outputs with business and security objectives.
PIRs are classified based on their time horizon and strategic impact
- Long-Term PIRs – Strategic intelligence (6 months to multiple years)
- Medium-Term PIRs – Operational intelligence (weeks to months)
- Short-Term PIRs – Tactical intelligence (real-time to a few weeks)
Requirements can come from interviews, questionairre's, Feedback, Observations, Bunsiness planning and a plethora of other means. The key really is to draft good intelligence requirements.
The Direction and Planning phase is essential for ensuring cyber threat intelligence (CTI) is effective, targeted, and valuable.
Key Takeaways
- ✔ PIRs drive intelligence collection and must be prioritized using MoSCoW and SMART.
- ✔ EEIs refine PIRs into specific intelligence data points for collection.
- ✔ An Intelligence Collection Plan (ICP) ensures intelligence gathering is structured, validated, and actionable.
- ✔ Intelligence must continuously evolve to address new threats and security challenges.
Without a clear direction, structured intelligence requirements, and effective planning, intelligence teams risk collecting irrelevant data, missing critical threats, and failing to support business security objectives. By implementing best practices in PIRs, EEIs, MoSCoW prioritization, and SMART refinement, organizations can ensure intelligence-driven security decision-making that proactively mitigates cyber risks.

Data collection in Cyber Threat Intelligence (CTI) is a critical process that must be efficient, agile, robust, and legally compliant. The ability to gather, validate, and analyze intelligence from both technical and human sources is fundamental to detecting, preventing, and mitigating cyber threats.
Some important things to consider: You cannot collect & monitor for everything! Therefore you need to find a balance and you will find yourself balancing the breadth against depth. Borad collection but shallow and detailed and narrow.
Topics we will cover
Collection Sources
Intelligence can come from many sources. Below we list the most common. It is important to note that depending on the souce you choose (of which could be multiple) then it is likely that one or more could change the dynaics of your intelligence collection. We will discuss legal frameworks later in this section, but for now it must be something you must factor in to your plan.
HUMINT
(Human Intelligence) – Intelligence collected from human sources through interviews, informants, or social engineering.
CHIS
(Covert Human Intelligence Sources) – Undercover agents or confidential informants who provide sensitive intelligence on criminal or cyber activities.
OSINT
(Open-Source Intelligence) – Intelligence gathered from publicly available sources such as news, social media, forums, and leaked databases.
SIGINT
(Signals Intelligence) – Intelligence derived from intercepted communications, network traffic, or electronic signals.
COMINT
(Communications Intelligence) – A subset of SIGINT focusing specifically on intercepted voice, radio, and digital communications.
ELINT
(Electronic Intelligence) – Intelligence gathered from non-communication electronic signals, such as radar systems, satellites, and military sensors.
TECHINT
(Technical Intelligence) – Intelligence related to foreign weapons, malware, encryption methods, and cyber attack capabilities.
FININT
(Financial Intelligence) – Intelligence tracking financial transactions, fraud, money laundering, and cryptocurrency flows to uncover cybercriminal or terrorist financing.
Legal Considerations
When collecting intelligence you must comply with legal and regulatory, particularly for HUMINT, SIGINT. Even with OSINT you should understand that there is still legal implications of collection. I suspect the majority of you reading this will be performing some sort of OSINT. Below I will detail some general legal considerations, pertaining to the UK. This should however prompt you to think about any laws or regulations relevant to your conuntry.
Legal OSINT collection means only gathering information that is publicly available, legally accessible, and compliant with UK data protection laws.
Illegal OSINT collection includes hacking, unauthorized access to systems, deceptive data gathering, and privacy law violations.
General Considerations
- ✔ The legality of accessing the data – Is the information genuinely public?
- ✔ The purpose of data collection – Is it for cybersecurity, corporate research, or investigative journalism?
- ✔ Data protection laws – Are personal details being processed, stored, or shared?
- ✔ Whether consent is required – Is data being collected from platforms that require explicit consent?
General Data Protection Regulation (UK GDPR) & Data Protection Act 2018
Specific to the above and to OSINT they cover the collection, processing, and storage of personal data.
Unlawful processing of personal data could result in fines. Scraping social media etc for personal information could also land you in trouble. Best practice is would be to anonymize or aggregate OSINT data to avoid processing personal inforamtion. You can read more on the Data Protection Action 2018 HERE & the UK GDPR HERE
Legal Considerations
- ✔ Organizations must ensure OSINT collection complies with GDPR’s data processing principles.
- ✔ Collecting personal data (e.g., names, email addresses, social media profiles) requires a lawful basis.
- ✔ Any data that identifies individuals (IP addresses, photos, phone numbers) is regulated.
- ✔ Using OSINT for profiling, automated decision-making, or tracking individuals may violate GDPR.
Computer Misuse Act 1990
- ✔ OSINT must not involve hacking, bypassing login credentials, or scraping data behind paywalls or authentication.
- ✔ Even if data is not protected by a password, using automated tools to bypass rate limits or terms of service may still be illegal
- ✔ Accessing leaked data from breaches may be unlawful, even if publicly available.
It goes without saying that any unauthorised access or using tools to extract data from computer systems without explcit permission is a big NO. Modifying (Addition, Deletions) to any data or meta data is not permitted. You can read more on the Computer Misuse Act 1990 HERE
Human Rights Act 1998 (Right to Privacy - Article 8)
- ✔ OSINT collection must not violate privacy expectations (e.g., scraping private social media groups).
- ✔ Even publicly available information may be subject to privacy rights if it is used to profile individuals.
The Human righs act protects individuls rights to privacy and personal data. Publishing OSINT data that invades that privacy could lead to legal claims. Using that data for doxxing, exposure or harrassment may also violate provacy rights. Always Avoid collecting and publishing OSINT data in ways that compromise individual privacy. You can read more on the Human Rights Act 1998 act HERE
Regulation of Investigatory Powers Act 2000 (RIPA)
- ✔ Government agencies (police, intelligence services) must obtain legal authorization to use OSINT for surveillance
- ✔ Private investigators and companies cannot engage in covert surveillance without legal justification.
- ✔ Tracking individuals’ online activities (e.g., social media monitoring) must comply with proportionality and necessity tests.
Monitoring individuals’ online behavior without lawful authority is illegal, intercepting privte communications is also illegal, any unapproved network monitoring is illegal and yes so is Phishing someone :) For more information on RIPA 2000 visit HERE
There are other legislations to consider also but I have focused on the main ones and while OSINT is a powerful tool, its use in the UK is regulated by strict legal frameworks to prevent privacy violations, unauthorized access, and misuse. By staying within legal and ethical boundaries, OSINT can be a valuable and lawful intelligence asset without exposing individuals or organizations to legal liability.
Data Varacity
In the conteext of cyber threat intelligence data veracity refers to the accuracy, reliability, and credibility of collected intelligence. In Cyber Threat Intelligence, ensuring data veracity is critical for making informed security decisions, preventing misinformation, and avoiding response efforts based on false or misleading intelligence.
Poor intelligence can lead to misattribution, wasted resources, and ineffective threat mitigation amongst many other issues. Threat actors can intentionnalu spread disinformation and deceptive content, plant flase flags to try and mislead analysis. It is crucial that you have a method to validate data before acting upon the intelligence.
I am firm believer that veracity is an ongoing continous process that applies to before, during and after intelligigence collection and analysis.
What impacts data veracity
- ✔ False or misleading intelligence – Can be intentional (disinformation) or accidental (misreported intelligence)
- ✔ Unverified sources – Unchecked OSINT, social media rumors, and manipulated threat reports.
- ✔ Outdated or stale data – Indicators of Compromise (IoCs) that are no longer valid.
- ✔ Deliberate deception – Cybercriminals using anti-forensics and false flag techniques.
As already mentioned, you need to make sure collected incoming data is credible and worth analyzing. So how could we do this?
Things to consider
- ✔ Evaluating source reliability – Ensuring that the intelligence comes from a trusted or verifiable source
- Cross-checking multiple sources – Avoiding reliance on a single data stream to prevent bias or misinformation.
- ✔Filtering out fake or misleading data – Using automated tools (e.g., anomaly detection, signature matching, and heuristic analysis) to remove junk intelligence.
- Tracking data freshness – Ensuring IoCs, attack indicators, and adversary behavior patterns are still active and relevant.
There are a couple of frameworks and resources we can use to our advantage. Two of which are failry well known and understood. Firstly there is the Admirality Code and the 5x5x5 National Intelligence Model
Admiralty Code - Source Reliability & Intelligence Credibility
| Code | Source Reliability |
|---|---|
| A | Completely reliable |
| B | Usually reliable |
| C | Fairly reliable |
| D | Not usually reliable |
| E | Unreliable |
| F | Reliability cannot be judged |
| Code | Intelligence Credibility |
|---|---|
| 1 | Confirmed by multiple independent sources |
| 2 | Probably true, confirmed by one source |
| 3 | Possibly true |
| 4 | Doubtful |
| 5 | Improbable, suspected deception |
| 6 | Credibility cannot be judged |
5x5x5 National Intelligence Model
| Source Reliability | Information Credibility | Handling Code |
|---|---|---|
|
A - Always Reliable B - Usually Reliable C - Fairly Reliable D - Not Usually Reliable E - Unreliable F - Cannot be judged |
1 - Confirmed by multiple independent sources 2 - Probably true, confirmed by one source 3 - Possibly true 4 - Doubtful 5 - Improbable, suspected deception |
1 - No restrictions on dissemination 2 - Only disseminate to specific groups 3 - Only disseminate to law enforcement or military 4 - Confidential, requires approval 5 - Secret, highly restricted access |
Variety, and Velocity of Data in Cyber Threat Intelligence
The 3 V's - (Volume, Variety & Velocity) must be considered when collecting data. The sheer amount of data that can be collected can get overwhelming very quickly. Volume refers to the amount of data collected. Variety refers to the different types and formats of data and the Velocity refers to the speed ata which data is generated, processed and dissemintated. We have a more in-depth look at processing in a later moodule.
Managing Large-Scale Intelligence Data
There are definitely challenges to consider when dealing with volume. Storage and Scalability, do you have the capacity to store and scale data collection? Do you understand or even prepareed for the costs? How will you collect data without overwhelming infrastructure?
Data Filtering Understanding that you will need to account for duplicate data, false positives and irelevant data.
Processing Power High-volume data requires advanced computing for analysis (e.g., Big Data, AI, ML). You can think about using automated filtering, AI-driven analytics, and scalable cloud storage to handle high-volume cyber threat intelligence.
Handling Different Intelligence Data Types
Variety refers to the diverse types of data collected in CTI, including structured, semi-structured, and unstructured data.
Types of Data in Cyber Threat Intelligence (CTI)
| Data Type | Example | Source |
|---|---|---|
| Structured Data | IoCs (IPs, hashes, domains), SIEM logs | Threat Intelligence Platforms, Firewalls |
| Semi-Structured Data | XML, JSON threat feeds | OSINT APIs, TAXII/STIX feeds |
| Unstructured Data | Dark web discussions, PDFs, Emails, Reports | HUMINT, Dark Web Forums, Incident Reports |
Challenges of variety can include Data Standardisation in that different formats require conversion and normalization, for example STIX and TAXII. (We will talk about these in detail later). Bein able to correlate across different data sources is also something to consider. Linking for example structured data with unstructed data to form a detection or pattern. There is also challenges around using different languages, understanding native context and slang especially when analysing text-based intelligence.
Some solutions could be use Threat Intelligence Platforms that are able to link events together. AI-Driven correlation and data enrichment toolsets.
Keeping Intelligence Fresh and Actionable
Velocity is an important factor. Timliness is key when it comes to cyber threat intelligence. The landscape shifts so quickly. Velocity refers to the speed at which cyber threat intelligence data is generated, collected, processed and acted upon. Challenges do rpesent themselves as with anything else. Real-time threat detection for exampple. Cyber threats evolve rapidly requiring instant near real-time data processing, Threat actors adapt quickly frequently changing IOC's, TTPs and C2 infrastructure. Being able to automate threat intelligence sharing is key to helpl prevent attacks and inform others.
Using real-time data pipelines, SIEM integration, SOAR automation, and threat-sharing communities (FS-ISAC, CERTs, MISP).
Collecting Data Securely
Secure data collection in Cyber Threat Intelligence is essential for protecting the confidentiality, integrity, and availability of intelligence sources and its operations. Whether collecting from open-source intelligence, human intelligence or any other, CTI teams must implement security measures to protect against exposure, legal violations, and adversary counterintelligence efforts.
You have to make some considerations, you should have at least thought about these in the planning & direction stage to some extent. Operation security and staying anonymous, especially making sure your analysts are protected from tracking, retaliation or accidental exposure. We've touched on the legal and ethical side of things. Preventing data breached and unauthorised access with appropriate storage, and awareness of anti forensic techniques and being able to scale efficiently.

Processing is the pivotal stage in the intelligence lifecycle where raw collected data is transformed into a usable format for analysis. After information is gathered from various sources, it is often messy, inconsistent, and overwhelming in volume. The processing phase organizes, cleans, and augments this data so that intelligence analysts can make sense of it. In essence, processing bridges the gap between collection and analysis by turning disparate bits of information into structured, reliable inputs.
Without effective processing, even the best data collection efforts fail to yield actionable intelligence – unprocessed data is simply noise. This stage is especially critical in today’s big-data environment, as modern organizations collect massive amounts of information (network logs, social media feeds, sensor data, etc.) that must be refined into meaningful insights. An effective processing workflow enables analysts to trust the integrity of the data and spend their time on interpretation rather than data cleanup.
Key Components of Processing: In practice, data processing comprises several key components or sub-tasks. This chapter will focus on three major components – Data Normalization, Data Validation, and Data Enrichment – and discuss best practices and challenges associated with each. By mastering these steps, intelligence professionals (from beginners to seasoned experts) can ensure their analyses are built on a solid foundation of high-quality data. We will also touch on common hurdles such as handling large data volumes, data format diversity, and maintaining data integrity, as well as ways to overcome these challenges (like automation and standardization). Throughout, we’ll incorporate real-world examples to illustrate processing in action and provide practical tips for implementing robust data processing pipelines.
1. Data Normalization
Data normalization is the process of standardizing data into a consistent format, structure, and unit system. In an intelligence context, normalization means converting diverse data into a common form so that comparisons and aggregations become meaningful. Sources of intelligence can vary wildly – one feed might list a date as “2025-03-11” while another uses “March 11, 2025”; or network logs from different vendors use different field names for the same concept. Normalization resolves these discrepancies by enforcing uniform conventions.
Some best practices
Use Standard Schemas
Leverage common data models or schemas (for example, the STIX format for threat intel) to map data into a shared structure. Using widely adopted standards accelerates integration of new data sources
Automate Format Conversion
Employ scripts or tools to automatically convert units (e.g., all timestamps to UTC) and parse text into fields. Many organizations use ETL (Extract, Transform, Load) tools or threat intel platforms that have built-in normalization features.
Maintain a Data Dictionary
Clearly document the canonical format for each data attribute (date format, coordinate system, naming conventions, etc.). This reference helps the team enforce consistency and is especially useful when onboarding new analysts or sources.
Handle Multiple Languages
Normalization isn’t only about numeric formats; it can include translating or transliterating text from different languages. For example, ensuring names of persons or groups are consistently spelled or coded even if sources are in different languages
Challenges
Achieving perfect normalization can be difficult. Different sources may have conflicting information or levels of granularity. There’s also a risk of losing nuance – if you over-normalize, you might strip away contextual details. Analysts must decide what level of standardization is needed without discarding meaningful anomalies. Additionally, new data formats constantly emerge (especially in technical intelligence), requiring ongoing updates to parsing and conversion rules. Despite these challenges, normalization is a crucial first step that enables all subsequent analysis by putting data in a comparable frame.
2. Data Validation
Data validation in intelligence processing is the practice of ensuring the accuracy, integrity, and reliability of data before it feeds into analysis. Validation includes verifying that data entries make sense (e.g., checking if coordinates fall within valid ranges, or that a supposed malware hash is of the proper length), cross-checking information against multiple sources, and removing or flagging erroneous, false, or irrelevant data. In simple terms, this step asks: “Can we trust this data?” Intelligence analysts often refer to the classic evaluative criteria: reliability of the source and accuracy of the information
Why it matters
Without validation, an intelligence product can be led astray by faulty data. Consider an example: if a threat feed reports an IP address associated with malicious activity, but that IP was recorded incorrectly (typo or formatting error), acting on it could waste resources or even cause harm (blocking the wrong address). In counterterrorism intelligence, if a source misidentified a location of a meeting, an entire operation could misfire. Thus, validation acts as a quality gatekeeper. It “ensures integrity, accuracy, and removes errors or inconsistencies” in the dataset (as the chapter outline emphasizes). In cyber threat intel, teams use validation to filter out false positives — e.g. confirming that an indicator truly is malicious and not a benign artifact.
Some best practices
Source Reliability Grading
Adopt a system to rate how trustworthy sources are. For instance, intelligence agencies use letter-number scales (like “A1” for completely reliable source with confirmed info). During processing, tag incoming data with the source reliability and past performance, and treat unverified sources with caution.
Cross-Verification
Whenever possible, validate critical pieces of information by checking multiple independent sources. If two or three separate sources report the same IOC or the same event details, confidence in its validity increases significantly
Automated Data Quality Checks
Implement rules to catch anomalies (e.g., an IP address outside normal ranges, or a field that should be numeric containing letters). These automatic validators can flag or discard obvious mistakes in datasets – for example, duplicate records, corrupted entries, or values that violate known logical constraints.
Human Review for Context
Some aspects of validation require human judgment. Analysts should quickly review processed data for anything that “looks off.” This could involve sanity-checking a list of top threats generated from data – does it align with analysts’ contextual knowledge? If a piece of intel dramatically contradicts established understanding, it merits a closer look (either it’s a breakthrough or a bad data point).
Challenges
One major challenge is that validation can be time-consuming.( seriously!) In fast-paced environments there’s pressure to disseminate intel quickly, and exhaustive validation might slow things down. It’s a balancing act between timeliness and accuracy. Another challenge is dealing with intentionally deceptive data, adversaries may feed false information to mislead. Analysts need to be wary of such attempts by validating through trusted channels. Additionally, some intelligence (especially exploratory or early-warning intel) comes with inherent uncertainty, the saying 'not everything can be 100% confirmed' is true. In those cases, validation might involve attaching estimates of uncertainty or confidence levels rather than binary true/false labels. The key is to be transparent about data quality, validated data moves forward, while anything dubious is either excluded or clearly annotated as low confidence. This practice prevents flawed data from propagating through the intelligence cycle. Bad data in = bad data out
3. Data Enrichment
Data enrichment is the process of augmenting raw data with additional context, metadata, or supplementary information to enhance its value. Enrichment takes a piece of collected data and adds layers of information that make it more informative and actionable. For example, if an intelligence report collects a suspicious domain name, enrichment could involve adding who registered the domain, when it was first seen, known associated threat actors, and any related IP addresses. In essence, enrichment turns isolated data points into contextualized intelligence by linking them to the bigger picture.
Why it matters
Enrichment addresses the “so what?” of data. A single data point in isolation might have limited meaning, but when enriched, it can reveal significance. For instance, a raw piece of SIGINT (signal intelligence) might be just an intercepted phone number, but enrich it with subscriber information, call records, and the known network of contacts, and suddenly you have a lead on a threat group’s communication chain. In cyber intelligence, enrichment is crucial because raw technical data (like a hash or an IP) is often not self-explanatory. By enriching an IOC with context (malware family it’s associated with, whether it’s been seen in recent attacks, which industries were targeted, etc.), analysts can prioritize and act on it effectively.
Common Enrichment Techniques
Metadata Tagging
Adding metadata such as time stamps, geo-coordinates, classification labels, source reliability tags, etc. For example, when processing social media intelligence, enrichment might attach sentiment scores or identifiers of the poster’s affiliation.
Contextual Information Linking
Connecting data to known entities or records. An address or personal name collected could be enriched by linking to a database of known suspects, or a cyber IOC could be linked to a known malware signature or threat actor profile. Pattern and trend data might be added here – e.g., “This IP has been part of a botnet observed in a trend of DDoS attacks last month.”
Threat Scoring
Many organisations enrich technical indicators with risk scores (often on a 0-10 or low/med/high scale) to quickly convey how dangerous or relevant an item is. Scoring often considers factors like how widely an indicator has been seen, how recently, and in what contexts. This helps triage data for analysts.
External Data Integration
Pulling information from external sources to add to internal data. This could be as simple as doing a WHOIS lookup for a domain, or as advanced as integrating intelligence feeds. By combining a variety of data sources can drastically increase the view.
Challenges
Enrichment can sometimes introduce bias or error( we cover this in a later module Threat Analysis Methodologies & Biases). If an enrichment source is outdated or biased, it might color the intelligence incorrectly (for example, an old threat database might label an IP as malicious when it is no longer, resulting in false alarms) - This is a big issue today!! There’s also the risk of information overload, too many contextual details can overwhelm analysts or end-users of intel. Finding the right level of enrichment is part art, part science, it improves with feedback (analysts and consumers can indicate what additional info is truly useful). Another challenge is technical, linking across different data types is not trivial (how to join an unstructured text mention of a person with a structured database entry, etc.). However, advanced analytics and entity recognition tools are making this easier, automatically connecting data points into knowledge graphs. Enrichment, when done well, significantly boosts the value of intelligence – it turns raw data into a story, a narrative that can drive decision-making.

After data has been collected and processed into a clean, enriched form, it enters the analysis stage, which is often considered the heart of the intelligence cycle. Analysis is where information is examined, interpreted, and transformed into finished intelligence – in other words, converting data into insight. In military doctrine, analysis is defined as “examining relevant information using reasoning and analytic techniques to reach a conclusion or determination”. This stage is crucial because it’s where human judgment and expertise come into play to find meaning in the data. An effective analysis phase takes the outputs of processing (which should be relevant and validated data) and applies critical thinking, analytical methods, and domain knowledge to answer the intelligence questions at hand.
In this chapter, we will explore key analytical methods: Pattern Analysis, Trend Analysis, Impact Assessment, and Risk Analysis. These represent core techniques or lenses through which analysts examine information. We’ll discuss how each method works, provide examples of their use, and highlight tools or best practices associated with them. Additionally, we will look at effective methodologies and tools used in intelligence analysis – from structured analytic techniques to software that assists in analysis – ensuring that both beginners and veteran analysts can sharpen their analytical tradecraft.
Analysis Methods
- Pattern Analysis
- Trend Analysis
- Impact Assessment
- Risk Analysis
1. Pattern Analysis
attern analysis is an analytical method focused on identifying and examining recurring elements within a dataset – the repeated trends, common features, or regular behaviors that emerge from the information. In an intelligence context, pattern analysis often means looking for commonalities across incidents or data points to see if they indicate a larger systematic occurrence or the signature of a particular actor. For example, crime analysts use pattern analysis to link crimes with similar modus operandi, potentially pinning them to the same perpetrator. Cyber threat analysts look for patterns like repeated attack techniques or infrastructure usage that can tie multiple attacks to a single threat group or campaign. Essentially, pattern analysis asks: “Have we seen this behavior before, and does it connect to other events?” Identifying a pattern turns isolated events into a narrative – it provides understanding that can lead to attribution (who is behind it), prediction (when/where it might happen next), or explanation (why it’s happening).
Best Practices for Pattern Analysis
Aggregate and Compare Data
Ensure you have data pooled in a way that makes comparison possible (this hearkens back to normalization in processing). Pattern matching is much easier when data points share a structure. Visualization tools, like link charts or timelines, can help highlight patterns by laying out data in space or time.
Use Technology for Detection
Modern analysts have the aid of algorithms for pattern recognition. Tools can scan large datasets (like years of incident reports or network logs) to surface clusters of similarities that a human might miss. For instance, machine learning can detect patterns of life anomalies – say, a user account logging in at odd hours in a pattern that matches known insider threat cases.
Be Aware of Randomness
Not everything that looks like a pattern is meaningful – sometimes coincidences happen. Analysts should use statistical reasoning to gauge if a pattern is likely due to chance or indicates a real connection. A helpful tip is to seek additional evidence supporting the linkage.
Document Patterns
When a pattern is identified, document its characteristics clearly (who/what/when/where/how repeated) and track new occurrences against it. This builds a knowledge base of known patterns (like template cases) that new intel can be quickly compared against. Many threat intel teams maintain profiles of threat groups (Think Mitre Att&ck) which essentially describe the known pattern of that group’s operations
2. Trend Analysis
Trend analysis is the examination of how variables or indicators change over time, aiming to understand the direction, rate, and significance of those changes. In intelligence, trend analysis often focuses on temporal patterns – is a particular threat increasing or decreasing? Are incidents becoming more frequent? How are adversary tactics evolving year over year? While pattern analysis often looks for repeating units or similarities, trend analysis is about trajectory and momentum over time. It provides a time-lapse view that can highlight emerging issues or the fading out of others.
Trend analysis is crucial for forecasting and strategic planning. By understanding how something is changing, analysts can project future states or at least alert decision-makers to where things are headed. For example, if trend analysis reveals a doubling of ransomware attacks every month, one can warn that this trajectory means a critical situation in a few months if not addressed. It turns intelligence from reactive (responding to what happened) to proactive (anticipating what is likely to happen).
Methods and Tools
Statistical Analysis
Basic statistical tools (mean, median, moving averages) help smooth out noise and see the underlying trend. Visualization is key: line graphs of incidents over time, heat maps over calendars, etc., make trends apparent at a glance.
Baseline Establishment
It’s important to know what “normal” looks like (baseline levels) so that deviations (upward or downward trends) stand out. For example, if typically an organization sees 5 phishing emails a week, but now it’s 20 a week for the past month, that upward trend is notable – but you only know it’s unusual if you had the baseline measured.
Longitudinal Data Collection
Ensure data is collected consistently over time. Gaps or changes in how data is collected can themselves create false trends. For instance, a country’s terrorism incident trend might appear to drop simply because reporting became less frequent, not necessarily because incidents truly dropped – an analyst must be cautious about such artifacts.
Regression and Modeling
For more advanced use, analysts might apply regression analysis to see correlations over time (e.g., do certain events correlate with rises in attacks?) or to model future projections (like extrapolating current trends forward, albeit with caution). In cyber intelligence, some use time-series modeling to predict when the next wave of attacks might come or how fast a malware is propagating.
Challenges
Trends can be influenced by external factors, and correlation is not causation. Just because two metrics trend similarly doesn’t mean one causes the other. It is an analysts job to avoid jumping to conclusions. It’s important to differentiate between a real trend and a temporary spike. Trend analysis is best combined with continuous monitoring and revision. It gives a sense of direction, but analysts must update their assessments as new data comes in.
3. Impact Assessment
Impact assessment often involves scenario analysis and use of expertise across disciplines. Analysts consider various dimensions of impact: financial impact, operational impact, reputational impact, safety/human impact, etc. They may use structured methods like SWOT analysis (to understand strengths, weaknesses, opportunities, threats) or more quantitative methods like loss estimates in dollars or lives. In cybersecurity, frameworks like FAIR (Factor Analysis of Information Risk) help estimate potential loss magnitude. In threat intelligence, an impact assessment might produce statements such as, “If this threat is realized, the impact is assessed as HIGH: likely to cause prolonged system outages and compromise sensitive data, leading to regulatory penalties and reputational harm.” One key part of impact assessment is communicating severity. Often organizations use impact ratings (like low, moderate, high, critical) combined with likelihood (from risk analysis) to prioritize issues. For instance, an intelligence report might say: Impact: High (a successful attack could shut down production for days).
Approaches
Impact assessment often involves scenario analysis and use of expertise across disciplines. Analysts consider various dimensions of impact: financial impact, operational impact, reputational impact, safety/human impact, to name a few. They may use structured methods like SWOT analysis (to understand strengths, weaknesses, opportunities, threats) or more quantitative methods like loss estimates in money or lives. In cybersecurity, frameworks like FAIR (Factor Analysis of Information Risk) help estimate potential loss magnitude. In threat intelligence, an impact assessment might produce statements such as, “If this threat is realized, the impact is assessed as HIGH: likely to cause prolonged system outages and compromise sensitive data, leading to regulatory penalties and reputational harm.” One key part of impact assessment is communicating severity. Often organizations use impact ratings (like low, moderate, high, critical) combined with likelihood (from risk analysis) to prioritize issues. For instance, an intelligence report might say: Impact: High (a successful attack could shut down production for days).
Challenges
Impact assessment can be speculative, it deals with “what ifs” and sometimes with incomplete information. It requires a careful balance between not underestimating a threat and not overestimating to the point of alarmism. To improve accuracy, it is good to use historical analogues, have we seen similar situations before and what impacts occurred then? For example, if assessing the impact of a potential malware outbreak, look at past outbreaks (like how WannaCry affected companies globally) to gauge possible outcomes. Another challenge is scope, threats can have indirect or ripple effects that are easy to overlook. Analysts should think more broadly about this, fo example a cyber attack not only causes IT downtime which can be considered a direct outcome but could also erode customer trust or stock prices, indirect impact. Engaging with different stakeholders can give a fuller picture of possible impacts.
4. Risk Analysis
Risk analysis in the intelligence realm is the process of evaluating potential threats in conjunction with vulnerabilities to determine the likelihood of an adverse event and its potential impact. It effectively combines the probability of a threat happening with the severity of its consequences. In other words, while impact assessment (above) focuses on consequences, risk analysis marries that with the chance that those consequences will occur. The output of risk analysis is typically a measure or rating of risk (often qualitative like low/med/high or quantitative if possible).
Methods and Tools
Qualitative vs Quantitative
Qualitative risk analysis uses categories and expert judgment. Quantitative attempts to assign numerical probabilities and monetary values to impacts (common in financial sectors). In intelligence, fully quantitative data is often lacking, so a semi-quantitative approach (like scoring) is common.
Threat/Vulnerability Pairing
Frameworks like Threat-Vulnerability-Asset matrices help ensure analysts consider where the organization is vulnerable. For instance, the threat of “state-sponsored hacking” might have high likelihood in general, but if your organization has strong cyber defenses, the residual risk might be lower. Conversely, a moderate threat can pose high risk if you’re very exposed to it.
Risk Registers
Many intel and security teams maintain a risk register – a living document listing identified risks, their ratings, and mitigation measures in place. This often ties into the feedback loop, as new intelligence can update risk ratings.
The relation to intelligence analysis
Intelligence analysis feeds risk analysis with up-to-date information on threats and context for likelihood. For example, intelligence might reveal that a previously low-activity terrorist group is now gaining strength – the analyst would update the likelihood of attacks from that group, raising the risk level. Likewise, feedback from how previous risk estimates panned out (were we surprised by something we rated as low risk?) can refine future risk models.
Challenges
Assessing likelihood is inherently difficult – it can verge on predictive analytics, which is imperfect. Analysts may disagree on likelihood (one might think an adversary will do X, another might think they’re bluffing). Combining empirical data with expert judgment is key. Additionally, cognitive biases can affect risk perception: e.g., recent events loom larger in mind (recency bias) and can cause analysts to overestimate those risks while underestimating others. Using systematic methods can mitigate this. Another challenge is that risk analysis must be continuously revised – it’s not a one-time task. As the environment changes (new threats emerge, old ones subside, new vulnerabilities introduced by say new technology), risk levels shift. A risk analysis should be a living process that is revisited regularly.

The Importance of Intelligence Dissemination
Dissemination is the stage where the hard-won insights of analysis are shared with the people who need to act on them. No matter how brilliant an intelligence assessment is, it holds no value if it doesn’t reach decision-makers, operators, or other stakeholders in time and in a format they can use. Remember this point! Timely and Accurate will be thrown around quite a bit. Dissemination is often described as the final step of the intelligence cycle - The finished article ready for delivery to the right audience so those who recieve can make and take the necesary decisions.
We will discuss different types of intelligence products – Alerts, Tactical Advisories, and Strategic Reports – each suited for different purposes and audiences. We’ll cover best practices for structuring these products, including formatting and writing style considerations (like clarity and BLUF – “Bottom Line Up Front”). We’ll also examine how to adjust language and technical detail for different audiences, balancing technical accuracy with accessibility.
Types of Intelligence Products
Not all intelligence deliverables are the same. They vary in immediacy, depth, and audience. Broadly, we can categorize them into a few types: (This is not exhaustive by the way)
Alerts
Definition
Alerts are immediate warning products that inform stakeholders of urgent threats or incidents requiring prompt attention. An alert is typically short, quickly disseminated (often outside regular reporting cycles), and focused on a specific issue that has just arisen or been detected. It’s the intelligence equivalent of a fire alarm – grab attention and prompt action now.
Characteristics
Alerts usually contain a clear statement of the threat, who/what is affected, and what immediate action is recommended. For example, a cybersecurity team might send an alert that “Malware X has been detected in our network – isolate server Y immediately”, or an intel unit may issue an alert “Credible threat reported against embassy Z – increase security posture”. Alerts often use high-priority communication channels: urgent emails marked with high importance, text message blasts, phone calls, or alarm features in dashboards. Because of their urgent nature, alerts need to be concise and unambiguous. Recipients should grasp the core message at a glance. Many organizations adopt a template for alerts to ensure consistency (e.g., a subject line that clearly indicates “ALERT:” and the topic, followed by a brief description and required actions). In terms of the intelligence cycle, alerts are disseminated often even as analysis is still ongoing (you might disseminate a preliminary alert and follow up with more details later), prioritizing timeliness.
Audience
Typically, alerts go to operational personnel who can act immediately. For instance, a SOC (Security Operations Center) staff, incident responders, field agents, or duty officers. However, depending on severity, high-level leaders may also be CC’d or separately briefed so they are aware of the situation (e.g., a CEO might not act on a technical alert but needs to know a critical incident is happening).
Tactical Advisories
Definition
Tactical advisories are short-term intelligence products that provide guidance for operational or tactical decision-makers. They are less urgent than immediate alerts but more focused and detail-rich about a current or emerging issue than strategic reports. The word “tactical” implies these advisories are meant to help front-line or operational units respond to threats in the near term. A tactical advisory often follows an alert or stands alone for threats that are important but not a drop-everything emergency. It may cover, for example, a newly discovered threat actor technique, a vulnerability that should be patched soon, or an update on a developing security situation with recommendations for mitigation.
Characteristics
Tactical advisories typically include: a description of the threat or issue, analysis of what it means for the organization or unit, and specific recommended actions or guidance to mitigate or address the issue. They may be a few paragraphs to a couple of pages long, often with bullet-point recommendations. The tone is actionable and direct. For instance, a tactical advisory in cyber threat intel might outline how a phishing campaign is targeting the finance department with certain lures, and advise, “Implement email rules to flag messages with these keywords, remind staff of phishing indicators, and verify any fund transfer requests verbally”. In law enforcement intelligence, a tactical advisory could be, “Over the next week, gang activity is expected to retaliate in Area B; patrol units should increase presence and use caution during night shifts” – plus details on known individuals or hotspots. One could think of tactical advisories as analogous to “bulletins” or “briefs”. They balance information with immediate utility. They often have a semi-structured format: situation/background, analysis, recommendations.
Audience
These are aimed at practitioners and operational leaders (e.g., security team leads, incident managers, field commanders, etc.). The language can assume a moderate level of technical or domain knowledge because it’s going to people who work in security or operations daily. However, it should still be clear and not overly jargon-laden, because within any team there can be varying levels of expertise. Tactical advisories can also be shared across organizations (e.g., through Information Sharing and Analysis Centers - ISACs - industries share tactical advisories about threats hitting one company so others can prepare).
Strategic Reports
Definition
Strategic reports are longer-term, comprehensive intelligence products intended for leadership and policy or decision-makers who focus on big-picture implications. They are usually less about immediate action and more about informing strategic understanding, planning, and resource allocation. Strategic intelligence looks at trends, threats, and opportunities over a longer horizon (months, years) and often covers broader scope, such as geopolitical developments, industry threat landscapes, or forecasts of future risks.
Characteristics
> strategic report often takes the form of a formal analytical report or assessment. It may range from a few pages to dozens of pages for in-depth studies. It typically includes an executive summary (critical for busy execs to grasp the key judgments quickly), sections detailing the background and analysis, and often some discussion of implications and possibly high-level recommendations. The writing style is usually more narrative and expository, ensuring it provides context and explanation, not just bullet points. However, clarity is still paramount – strategic reports should avoid unnecessary technical detail that would confuse a non-specialist reader. According to our CTI training reference, Strategic Reports are “long-form analysis for executive stakeholders.”
They are high-level, and connect the dots between intelligence findings and business or security strategy. For example, a strategic threat intelligence report for a corporation might outline the threat actor groups that are likely to target the company, their motives, and what that means for the company’s risk in the coming year. It might analyze how the global political situation could lead to more cyber attacks in the sector, and advise leadership on strategic investments (like improving certain defenses or monitoring capabilities). In government, a strategic intel report might assess the stability of a region and options for policy, or an NIE (National Intelligence Estimate) that covers, say, the nuclear capabilities of a country and likely scenarios.
Audience
As noted, strategic reports are often for executives, senior officials, and policy makers. These individuals may not have technical backgrounds, so the report must convey the essence without assuming detailed prior knowledge of technical terms. Jargon should be minimized or clearly explained. The focus should be on insights and their relevance to the organization’s mission or goals. For example, a CISO or CIO reading a strategic cyber intel report wants to know “What are the most serious threats on the horizon and what should we do about them in our strategy?” rather than the minutiae of malware code.
Strategic Reports
Long-form analysis for executive stakeholders
Tactical Advisories
Specific guidance for security teams
Alerts
Immediate notifications for active threats
Best Practices for Structuring Intelligence Reports
No matter the type of intelligence product, ertain writing and formatting best practices apply to ensure clarity, usability, and professionalism. Here are key principles and tips: (This is something that you develop and continue to improve upon)
If you're looking on how to practically build these products in my paid course, which can be found here. CTIMASTER
- ✔ Use Clear Headings and Organization. Just as this module is structured with headings, an intelligence report should be well-organized.
- ✔ Bottom Line Up Front (BLUF), This is a writing principle widely taught in intelligence and military circles. It means state your main point or conclusion at the very beginning of the product.
- ✔ Clarity and Conciseness is key. Write in a clear, straightforward style. Avoid long, convoluted sentences or overly technical jargon. The goal is to communicate, not to impress with big words.
- ✔ Writing Tone is important. Maintain an objective, professional tone. Intelligence writing is typically in third person, avoiding emotive language or unsupported judgments
- ✔ Precision in Judgments. Use estimative language carefully. Words like likely, unlikely, probable, possible should reflect the analyst’s confidence level. Many organizations have adopted the likelihood scale from intelligence community directives
- ✔ References and Evidence In an academic context, citations or footnotes might be used to show sources. In corporate or classified intel, you may refer to sources more vaguely if sensitive (like “Source A (reliable) reported X”).
- ✔ Review and Edit (goes without saying really) Always review the report for accuracy, clarity, grammar, and completeness. A typo or unclear sentence can undermine credibility or lead to dangerous misinterpretation in intel. If time permits, have a colleague proofread.

The continuous improvement phase where stakeholder feedback is collected and incorporated into the process.
Collecting Feedback
Gathering feedback requires deliberate effort and multiple channels. Stakeholders are often busy and may not spontaneously provide input, so the intelligence team should proactively seek it in convenient ways. Here are common methods for collecting feedback from intelligence consumers and partners:
Surveys and Questionnaires
Interviews and Debriefings
Direct Feedback Loops
Internal Team Feedback
Measuring Effectiveness
To truly understand how well the intelligence function is performing, qualitative feedback is essential but not sufficient. Establishing Metrics and Key Performance Indicators (KPIs) provides a more objective gauge of effectiveness over time. These metrics should align with the goals of the intelligence program, often reflecting qualities like timeliness, accuracy, relevance, and actionability of intelligence products (as the user prompt highlights).
Timeliness
Accuracy
Relevance
Actionability
Coverage
Completeness
Customer Satisfaction
Process Efficiencies
Process Improvement
Collecting feedback and measuring performance are only valuable if you act on that information. Process improvement is about implementing changes to the intelligence cycle based on what feedback reveals, in order to enhance intelligence accuracy, relevance, and overall value. Here’s how feedback can drive improvements in various stages of the cycle: